Mobile Hotspots
Abstract
Passwords have to be secure and usable at the same time, a trade-off that is long known. There are many approaches to avoid this trade-off, e.g., to advice users on generating strong passwords and to reject user passwords that are weak. The same usability/security trade-off arises in scenarios where passwords are generated by machines but exchanged by humans, as is the case in pre-shared key (PSK) authentication. We investigate this trade-off by analyzing the PSK authentication method used by Apple iOS to set up a secure WPA2 connection when using an iPhone as a Wi-Fi mobile hotspot. We show that Apple iOS generates weak default passwords which makes the mobile hotspot feature of Apple iOS susceptible to brute force attacks on the WPA2 handshake. More precisely, we observed that the generation of default passwords is based on a word list, of which only 1.842 entries are taken into consideration. In addition, the process of selecting words from that word list is not random at all, resulting in a skewed frequency distribution and the possibility to compromise a hotspot connection in less than 50 seconds. Spot tests show that other mobile platforms are also affected by similar problems. We conclude that more care should be taken to create secure passwords even in PSK scenarios.
Technical Report: “Usability vs. Security: The Everlasting Trade-Off in the Context of Apple iOS Mobile Hotspots” (PDF)
Authors: Andreas Kurtz, Daniel Metz and Felix C. Freiling
iOS App Hotspot Cracker
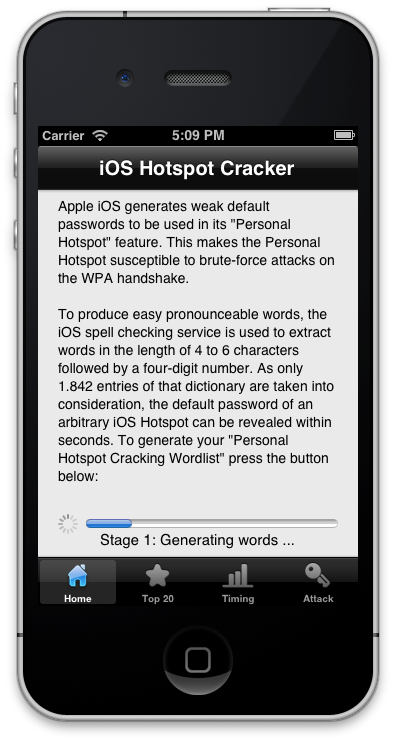
To automate the process of word list generation, we built the iOS app Hotspot Cracker. This app assists in generating an iOS hotspot cracking word list, which might be used in subsequent attacks on other hotspot users. The app also gives explanations and hints on how to crack a captured WPA2 handshake using well-known password crackers. Future releases might also automate the process of capturing and cracking hotspot passwords. As computing power on smart devices is limited, one solution is to involve online password cracking services like CloudCracker, to crack hotspot passwords on-the-fly.
Download: Source (Xcode Project, 679 KB)
Screenshots:
 |
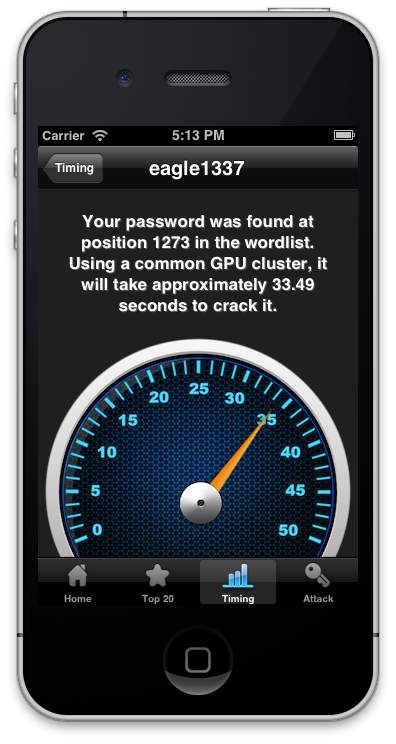 |
| The iOS App Hotspot Cracker assists in generating an iOS hotspot cracking wordlist (left image). A GPU cluster composed of four AMD Radeon™ HD 7970 can cycle through around 390.000 guesses per second. As the hotspot wordlist consists of only 1.842 entries followed by a four-digit number, there are only around 18.5 million possible combinations. This means, that a GPU cluster will crack an arbitrary password in less than 50 seconds. Users can enter their default hotspot password into the Hotspot Cracker app to estimate the average cracking time (right image). | |